If malicious files (viruses) were found on your site and you don't know what to do, rest assured—we will teach you in this article!
On Stage, we guarantee the blocking of DDoS attacks, which prevents your website's resources from being used for purposes other than your customers' access. This ensures that there is no server overhead and unavailability.
However, we are unable to guarantee the security and reliability of third party elements—such as plugins, themes and code changes—and these are the most likely entry points for malicious files.
Here, we will teach you how to clean these files in the best possible way!
First of all, it is important to note that this maintenance is ideally done by a developer, as there are several details to pay attention to in the process that can break your website.
So let's follow a step by step:
1. Before starting the process, it is essential to have a website backup available so that, in case you make an improper change and break it, you will be able to go back to the beginning and restart the process.
On Stage, we have automatic daily backups with a history of 7 days for the Pro plan, 15 days for the Business plan and 30 days for Enterprise.
As your backup is already done, you do not need to save a new one. However, if you wish to have one on hand, just ask at help@rockcontent.com.
2. Access your FTP and delete the infected files. You can find the name of these files in Rock's report:
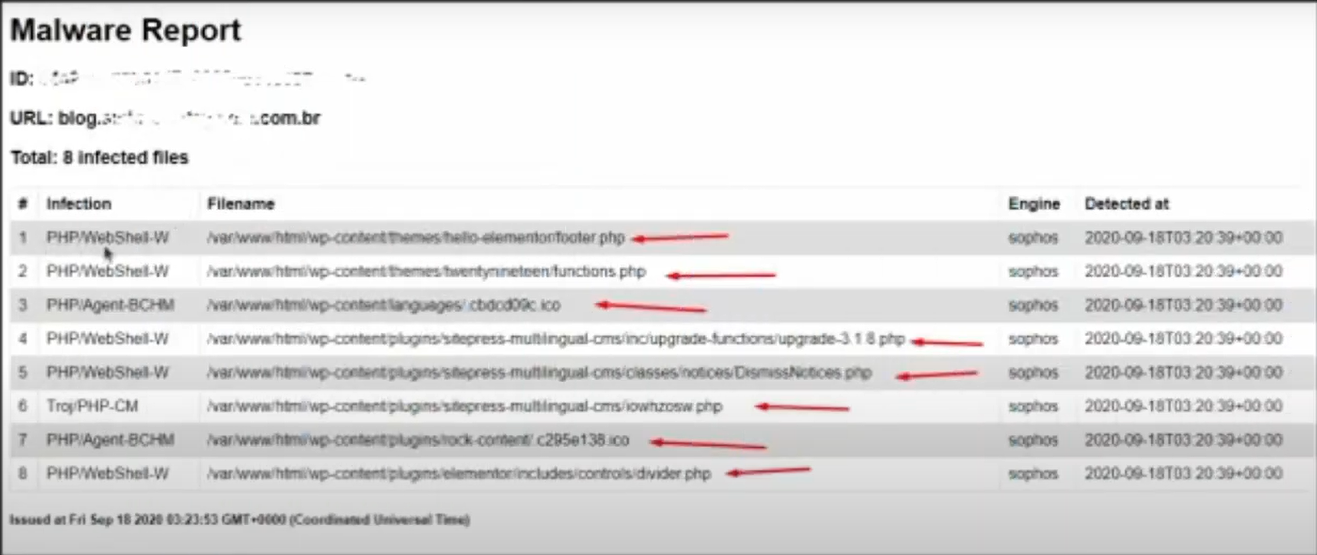
Each of the elements indicated by the arrows is the name of a file that must be deleted.
3. Delete any user that you do not recognize within your WordPress administrative panel.
4. Change the password of all users.
5. Check if there is any folder on your FTP with a strange name (such as random characters) and delete it.
6. Install a security plugin on your WordPress. In this article we teach you how to choose a suitable option.
7. Check if your FTP has any of the most common backdoors used by hackers.
These are usually files with names similar to real WordPress files, but located in directories they shouldn't be in, such as the wp-config.php file and the wp-content/themes, wp-content/plugins, and wp-content/uploads folders.
Some of the most common backdoors are:
- base64
- str_rot13
- gzuncompress
- eval
- exec
- system
- assert
- stripslashes
- preg_replace (with /e/)
- Move_uploaded_file
8. Lastly, it is recommended—but not mandatory—that you delete and reinstall all your WordPress plugins and themes to ensure that any vulnerabilities are closed.
After going through this removal process, let us know at help@rockcontent.com so that we can run another scan and verify that all malicious files have been removed from your site.
If you prefer, review the process in this video:
Do you have any further questions? Just contact us at help@rockcontent.com.br :)
.png?height=120&name=rockcontent-branco%20(1).png)